Who's watching me play? A rudimentary look into Roblox Player's data collection
Roblox is a fascinating software ecosystem with occasionally questionable security and privacy practices. The company has gone to great lengths to prevent reverse-engineering and exploitation through the inclusion of VMProtect obfuscation, as well as in-house and third-party anticheat systems (which lead to great pains for Linux gamers for several years). Additionally, much of its networking protocol, though based on the publicly available RakNet, is undocumented. However, I have managed to devise a method to decrypt the HTTPS traffic produced by the executable itself giving an initial look into the user data collected. Do note, however, that this article is not at all-encompassing. During the development of the Grapejuice Flatpak, I discovered the usage of ptrace() by Roblox Player, potentially indicating other nasty forms of data collection. But I digress...
Breaking it down: Decrypting the HTTPS data
My current method has only been tested on a Linux system with WINE, though it is theoretically possible to replicate on Windows. The only required software are Wireshark and WINE. The technique is as follows:
- Begin a Wireshark capture session and filter by HTTP (use filter "http || http2 || http3")
- Pass SSLKEYLOGFILE="/path/to/file" environment variable in WINE
- This can be done through the [env] field in Vinegar!
- Load the keyfile into Wireshark
- See this source for more information
- You will want to use "(Pre)-Master-Secret" field
- Observe the decrypted payload
- Of particular interest are the HTTP/JSON messages...
Under the Microscope: Reading the decrypted telemetry
Roblox's network traffic is rife with telemetry. In roughly 5 minutes of gameplay, I recorded just over 450 HTTP messages. Let's have a look at some particularly notable packets. CAUTION: Before sharing your own session data, make sure you did not include your ROBLOSECURITY cookie! This cookie can be used by others to log into your account, if shared!
Initial Join Data
-
-
-
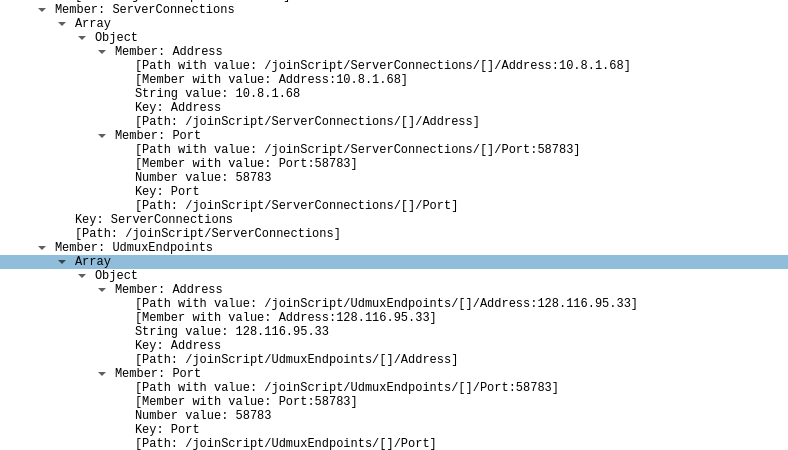
On initial launch and join, some data including server connection information and RakNet encryption data is sent. This is innocuous and can be easily viewed from Roblox internally by pressing Ctrl-Shift-F3. However, one should take note that Roblox keeps strict tabs on program timing (seen in timings.png), counting and reporting FPS even when the program is idle.
Erm...My email?
-
-
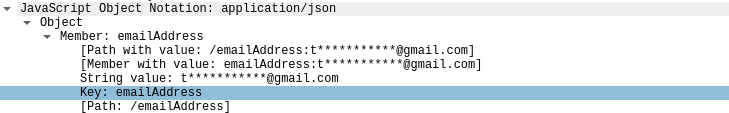
It seems odd to send my email address (thankfully truncated to the client). However, as this is HTTPS encrypted data, this is a safe practice, especially as most of the email is hidden.
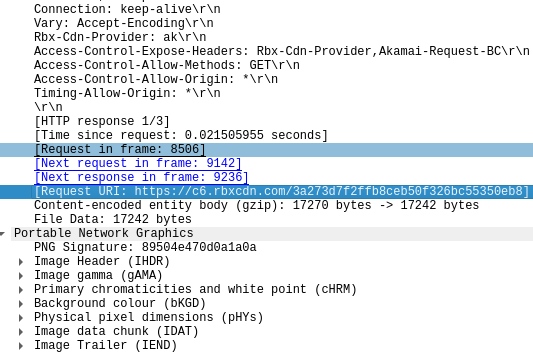
Yoink, your assets are mine
-
-
Though unrelated to data collection, this packet is of note. It appears that any assets not transmitted through RakNet (such as baseplate data or other Roblox internal datatypes) are transmitted through HTTP. I have recovered meshes, audio files, animations, and images from simply visiting a game. This could make stealing assets trivial; there would no longer be a need to exploit a game before acquiring its data.
Control Freak!
-
-
-
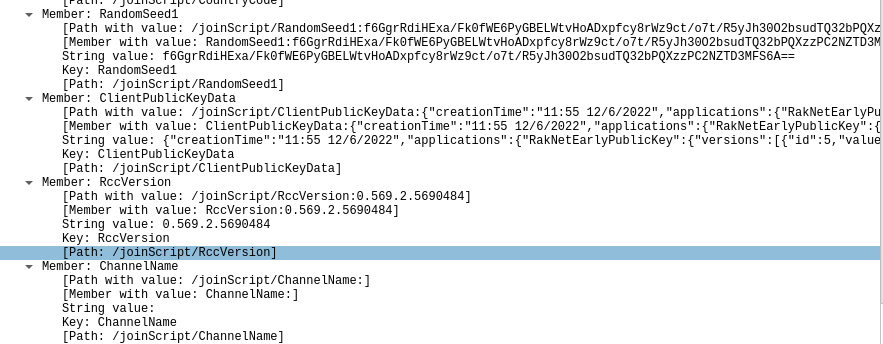
As a reiteration of my previous point, Roblox seems to highly value timing data. The amount of time the user keeps the developer console open, the system memory frame time, and the user's timezone are all transmitted frequently.
Caught a big one!
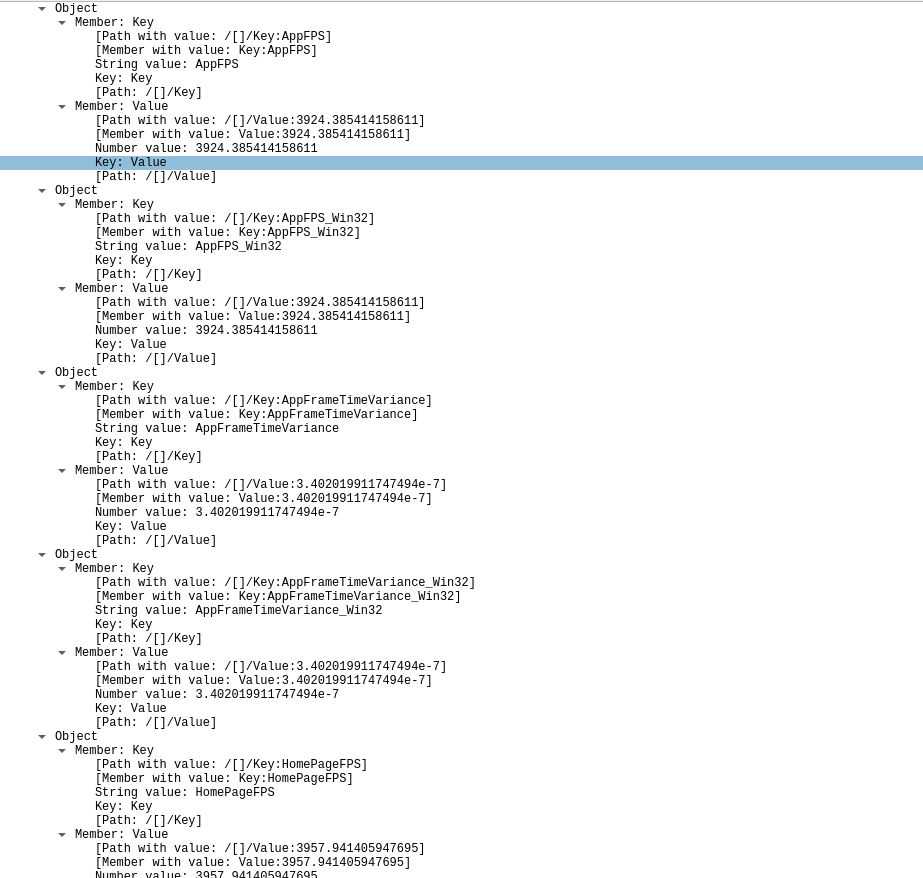
Telemetry,datacenterid=370,application=Client,ostype=Win32,osname=WINE32,baseurl=.roblox.com,channel=production,appversion=0.569.3.5690486,type=counter,streamingenabled=disabled,corescriptversion=5345954812.6288 location="US",playSessionId="0d2fa120-2b10-4c81-9b83-56056dee2873",placeid=12011578353i,placeversion=4i,device="PC",osversion="8.5",logguid="0/0.569.3.5690486_20230404T044323Z_Player_673AB_last.log",sessionDuration=34.623824,clientTimestamp="2023-04-04T04:43:58.291Z",serverIp="10.208.11.134",port="56134",mult=1.000000,SoundReportInfo-ParentAdded-Block=9i,SignalR_InvalidSequenceNumber_PresenceBulkNotifications=3i,SignalR_TotalSequenceNumber_GameCloseNotifications=1i,SignalR_TotalSequenceNumber_PresenceBulkNotifications=3i
This large chunk of data, sent to https://client-telemetry.roblox.com/ includes what is essentially a short summary of the user system. Of particular note is the osname=WINE32 identifier, which implies the active tracing and monitoring of Linux players. Curiously, the server IP listed appears to be on a local subnet; perhaps it is datacenter specific.
Sum up
Again, this report is not entirely comprehensive. Countless packets were omitted for the sake of brevity. However, the constant monitoring of the user's system's timing and performance is excessive and may lead to performance degradations or network charges. I will definitely point out that one should definitely employ the RCO patchset (included with Vinegar) if there is a desire to reduce telemetry. In my own tests, it lead to hundreds less telemetry packets being sent. Of greatest importance, at least in my opinion, is the unobscured transfer of game data through HTTP instead of RakNet, which could be used to acquire assets for nefarious purposes.
First published Apr 3
